- System Software Blocked From Loading Mac Allow Not Working
- Mac System Software Was Blocked From Loading System

In our recent post titled macOS 10.13 High Sierra Significantly Improves DisplayLink Performance & Stability we talked about how the latest update to macOS improved behavior when using a DisplayLink product (such as the Plugable UD-ULTCDL docking station). To go with that, we wanted to take a moment to discuss the Gatekeeper security feature introduced back in OS X 10.7 which has gone through some changes in High Sierra that may affect installation of some 3rd party device drivers used in devices from Plugable and other device manufacturers. For Plugable, the issue will only impact our products which don’t have drivers already built-in to macOS, such as our USB Docking Stations, USB Graphics Adapters, and USB Ethernet Adapters. Essentially this issue can affect any extensions not developed by Apple. Thankfully if you encounter this, there’s a simple process to fix. Keep reading for additional information and instructions.
In macOS 10.13 High Sierra, when installing new software and extensions, Gatekeeper now requires users to manually approve any new third-party extension before the computer can load and make use of the extension that was installed. This is important as many devices rely on extensions to function properly, and in some circumstances it can look like the software to power a device was installed but the device still doesn’t work. When this happens, users will see the below message:
Mac mail app not getting new mails. Click and highlight the 'Sent' folder for your account. Follow these simple steps to configure this:.
In macOS High Sierra, System Prefs Security, it says 'Some system software was blocked from loading. I see a list there of three developers, and I don't recognize all of them. I'm guessing these are kext files in /L/E or /S/L/E, but how can I identify exactly which kext corresponds to each developer name? I am running a Mac mini in a datacenter 5000 km from my location and I am using Remote Desktop to run and manage it. When I installed Google Drive File Stream it stopped working and I got the advice that I need to allow it run. But nothing happens when I click 'Allow'. Somebody told me it was because I use Remote Desktop (same with TeamViewer). Apr 27, 2020 When prompted, enter your Mac User Name and Password and then Unlock the preferences; Click 'Allow' next to the message 'System software from developer 'Palo Alto Networks' was blocked from loading.' This article provides instructions to enable kernel extensions that have been blocked during software installations in macOS. Apple introduces a new security mechanism in macOS High Sierra 10.13 that requires a user’s approval before loading third-party kernel extensions (kexts). Several LaCie programs are impacted by this macOS feature.
If you suspect Gatekeeper is preventing an extension from loading, follow the below steps:
- Open System Preferences and navigate to the Security & Privacy section.
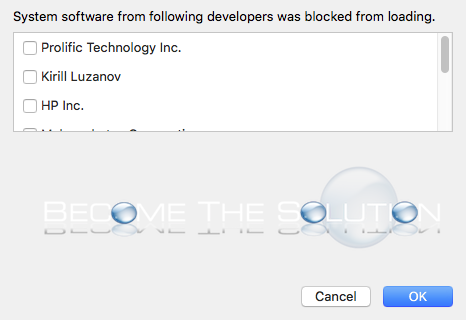
- In the General tab, look for a message at the bottom of the window stating “System software from developer DEVELOPER NAME was blocked from loading”, like in the screenshot below:
For Plugable products, the developer listed in the message should be “DisplayLink Corp” for DisplayLink powered products (such as docking stations that do not use Thunderbolt 3 technology) and “WEI LU SU” for Plugable ethernet adapters that use ASIX chipsets (as of the time of writing this, all Plugable USB network adapters use ASIX chipsets). - Click Allow, and from there macOS should now be able to properly load and use the extensions and software that were installed.
- Test things out! In some instances, you may need to restart the computer for the extension to properly load. So if it doesn’t work immediately, reboot the computer and the extension should load correctly.
Once an extension from a developer has been allowed, this makes the developer a ‘trusted’ source. Meaning that future extensions that are installed from the same developer should not be prevented by Gatekeeper from loading and should not need to have these steps repeated. However, software and extensions from other developers will encounter this same issue and you will need to follow these same steps.
For additional information on Gatekeeper and the behavior described in this post, check out the below Apple and DisplayLink support documents!
Feel free to share your experiences with High Sierra in the comments below, and if you’re having issues installing driver extensions for any of your Plugable products, please email support@plugable.com and we’ll be happy to help!
macOS Compatibility
Unfortunately, due to changes in macOS 10.15 Catalina and support for third-party drivers, we are unable to continue support for macOS with our ASIX USB to Ethernet adapters (USB3-E1000, USBC-E1000, USB2-E1000, USB2-E100, USB2-OTGE100). Our USB3-HUB3ME and future USB to Ethernet adapters will use Realtek based chipsets that utilize drivers built into macOS.
macOS High Sierra 10.13 introduces a new feature that requires user approval before loading new third-party kernel extensions. This feature will require changes to some apps and installers in order to preserve the desired user experience. This technote is for developers who ship kernel extensions to users and system administrators who need to install kernel extensions.
Introduction
macOS High Sierra 10.13 introduces a new feature that requires user approval before loading newly-installed third-party kernel extensions (KEXTs). When a request is made to load a KEXT that the user has not yet approved, the load request is denied. Apps or installers that treat a KEXT load failure as a hard error will need to be changed to handle this new case.
Approval is automatically granted to third-party KEXTs that were already present when upgrading to macOS High Sierra.
Note that approval doesn't guarantee that a KEXT is compatible and won't panic the system. The reason this feature exists is to give users more control over what KEXTs will load, which should reduce the number of panics.
In-Depth Explanation
This feature enforces that only kernel extensions approved by the user will be loaded on a system. When a request is made to load a KEXT that the user has not yet approved, the load request is denied and macOS presents the alert shown in Figure 1.
This prompts the user to approve the KEXT in System Preferences > Security & Privacy as shown in Figure 2.
This approval UI is only present in the Security & Privacy preferences pane for 30 minutes after the alert. Until the user approves the KEXT, future load attempts will cause the approval UI to reappear but will not trigger another user alert.
The alert shows the name of the developer who signed the KEXT so the user has some information to decide whether to approve the KEXT. This name comes from the Subject Common Name field of the Developer ID Application certificate used to sign the KEXT. Because of this, developers are encouraged to provide an appropriate company name when requesting KEXT signing identities.
When the user approves a KEXT, they are at the same time approving these other KEXTs signed by the same Team ID:
If the approved KEXT is located in an application's bundle, all other KEXTs signed by the same Team ID in the same application's bundle are also approved.
If the approved KEXT is located in the app's sub-directory inside
/Library/Application SupportMake app out of website mac. , all other KEXTs signed by the same Team ID found in that same sub-directory are also approved.All KEXTs in
/Library/Extensionssigned by the same Team ID are also approved.
Once approved, the KEXT will immediately be loaded or added to the prelinked kernel cache, depending on what action was blocked. Subsequent requests to load the KEXT will proceed silently as on previous macOS versions.
Approved KEXTs are tracked in a system-wide policy database through the team identifier in the KEXT's code signature and the bundle identifier from the KEXT's Info.plist, so updating a KEXT that has already been approved will not trigger a new approval request.
How This Affects KEXT Developers
Installers and applications that load kernel extensions may need to be revised to gracefully handle the kernel extension failing to load. Many products treat a KEXT loading failure as a hard failure. Some prompt the user to reinstall, some present a cryptic error message, and some simply don't function.
https://golpdf.netlify.app/logitech-mx-anywhere-mouse-mac-software.html. Starting with macOS High Sierra, installers and apps that load KEXTs should expect that KEXT loading will fail if the user hasn't approved their KEXT. Instead of treating this as an error, the user should be informed that they may need to approve the KEXT.
To determine if a KEXT has failed to load because it does not have user approval:
If you are using
kextutilorkextload, check for the exit code 27. In addition,kextutilwill produce the error messageSystem policy prevents loading the kernel extension.If you are using the KextManager APIs in
IOKit/kext/KextManager.h, check for the result codekOSKextReturnSystemPolicy.
How This Affects Enterprise App Distribution
For enterprise deployments where it is necessary to distribute software that includes kernel extensions without requiring user approval, there are two options:
If your workflow is based on imaging, boot into Recovery OS and use the
spctl kext-consentcommand. For detailed information about thespctlcommand, run the commandspctl help. This command can either disable the user approval requirement completely or specify a list of Team IDs whose KEXTs may be loaded without user approval. Thespctlcommand works in any installation environment, including Recovery OS and from NetBoot/NetInstall/NetRestore images.Note that the Team ID list maintained by
spctlis separate from the system-wide policy database.For workflows that leverage Mobile Device Management (MDM), please see the AppleCare support article Prepare for changes to kernel extensions in macOS High Sierra.
To reiterate, all third-party KEXTs that were already installed at the time of upgrading to macOS High Sierra are automatically approved and don't require any user action.
Document Revision History
| Date | Notes |
|---|---|
| 2018-04-19 | Updated for MDM changes in macOS 10.13.4. |
| 2017-09-08 | Updated for macOS High Sierra beta 8. |
| 2017-08-04 | Updated for macOS High Sierra beta 4. |
| 2017-07-12 | Updated for macOS High Sierra beta 3. |
| 2017-06-19 | New document that describes the user-approved kernel extension loading feature introduced in macOS High Sierra. |
System Software Blocked From Loading Mac Allow Not Working
Mac System Software Was Blocked From Loading System
Copyright © 2018 Apple Inc. All Rights Reserved. Audio to text converter software for mac. Terms of Use | Privacy Policy | Updated: 2018-04-19